Encrypting Attached EBS Volumes
Time and time again whenever I’m reviewing an AWS environment I’ve always noticed that many customers neglect enabling encryption features for data at rest for EC2 volumes and snapshots, RDS and even S3 buckets and their objects.
As with most cloud deployments it’s fairly easy to provision resources and run them for quite some time until you realize that a flag or toggle that could improve your security posture should have been selected at the time of provisioning.
Once a resource has been provisioned without enabling encryption at rest, the task of enabling encryption becomes a rather serious challenge.
In this blog post I’ll show you how to encrypt EBS volumes that are attached to EC2 instances. This is a fairly manual task that has to be done for each EBS attached volume, plan for downtime… It will take some time.
AWS has a feature that needs to be configured per region to enable EBS encryption by default. This can be found in the Account attributes tile under the EC2 Dashboard page. Now would be the perfect time to enable this feature for future deployments.
Back to the task at hand, encrypting an EBS volume that is attached to a running EC2 instance has a few steps.
Remediation:
- Navigate towards the EC2 console and select Volumes under the Elastic Block Store section.
- Select an unencrypted volume and then select the Actions button and from the dropdown select Create snapshot.
- Navigate towards Snapshots on the left-hand side under the Elastic Block Store section.
- Select the newly created snapshot, select the Actions button then select Copy snapshot.
- Under encryption, select the checkbox next to Encrypt this snapshot and proceed to select the Copy snapshot button at the bottom of the screen.
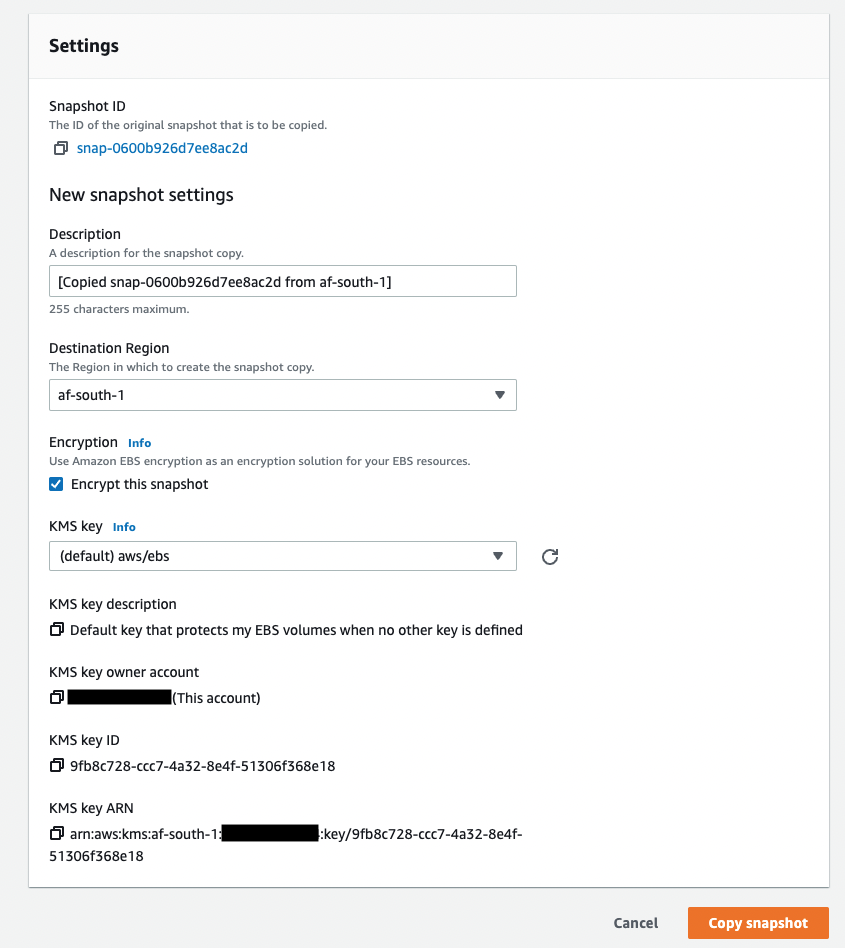
- Create a volume from the copied snapshot by selecting the snapshot then proceed to select the Actions button then select Create volume from snapshot. From the Create volume page, ensure to select the same Availability Zone where your EC2 instance was originally deployed in (Open another tab and verify the region), scroll to bottom of the page and select Encrypt this snapshot.
- Navigate towards Volumes, you’ll see the newly created encrypted volume in an Available state.
- Navigate back towards the EC2 Dashboard and select Instances under the Resources tile, select the instance that you intend to detach the unencrypted EBS volume and attach the newly encrypted volume, select the Storage tab and copy the Root device name to your clipboard.
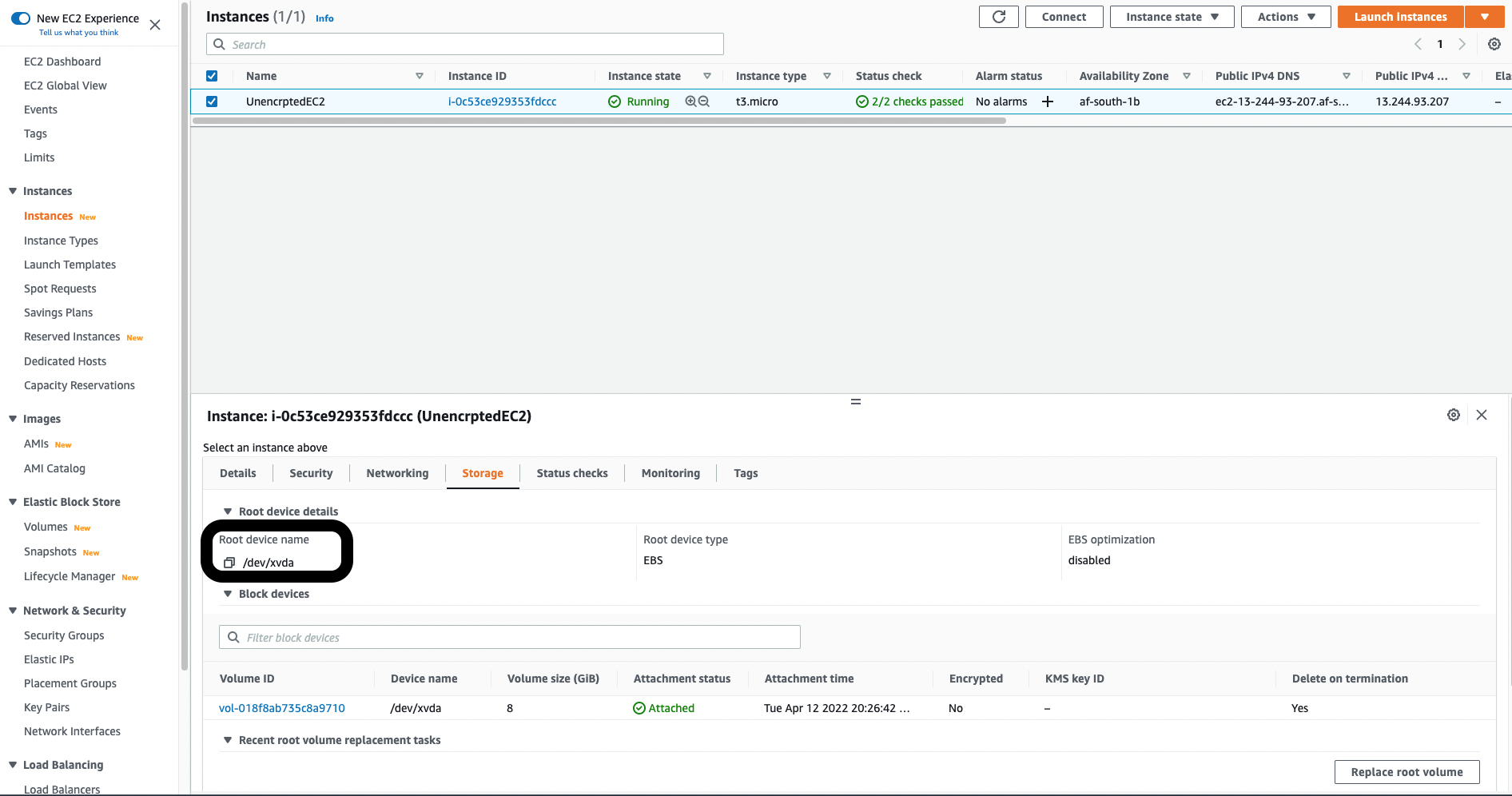
- Stop the running instance, then navigate towards Volumes under the Elastic Block Store section.
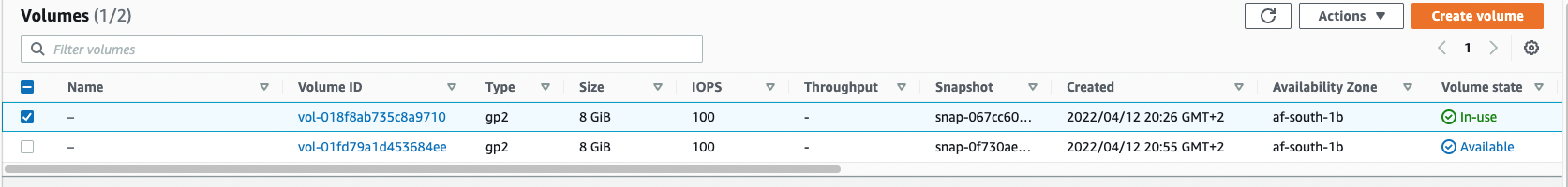
- Select the unencrypted volume, then select the Actions button and from the dropdown select Detach volume.
- Now select the encrypted volume then select the Actions button and from the dropdown select Attach volume, from the attach volume page, select your instance and in the Device name textbox paste the Root device name from step 8 and select the Attach volume button at the bottom of the screen.
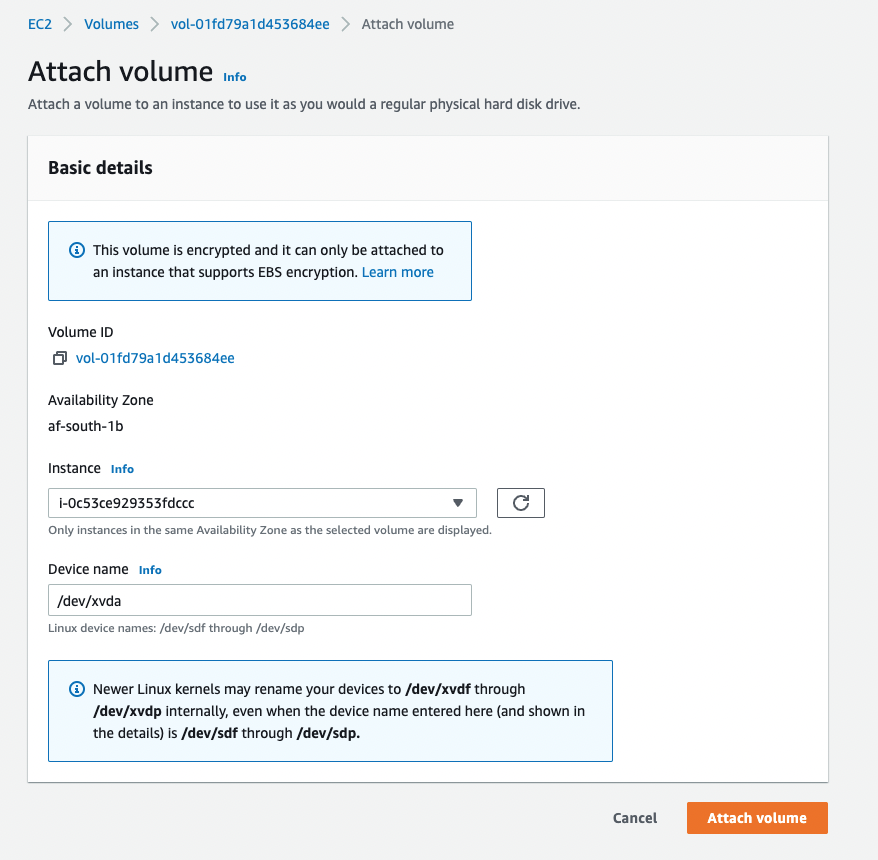
- The final step is to start your instance.
In 12 steps I’ve shown you how to encrypt an EBS volume that is attached to an EC2 instance, If you have a couple of EBS volumes this shouldn’t take long, just make a note of Root device name.
I’m having flashbacks of a customer that had over a 100 unencrypted volumes being used in production. That brings the conclusion to this blog post.
Encrypting Attached EBS Volumes
https://adrianthegreat.com/2022/04/12/Encrypting-Attached-EBS-Volumes/