The Power Of Lambda - A serverless approach to invalidating AWS CloudFront
It’s no secret that since I began my cloud journey in late 2018 i’ve been intrigued by serverless computing. At work i’ve even gone as far as designing and implementing a few Azure Functions that are used in production. I thought now would be the perfect time to write a blog post on a practical use case for AWS Lambda.
What is Lambda ?
Lambda is a function as a service offering from AWS that allows you to focus on writing code and letting AWS provision and maintain the underlying technology stack that your code runs on. As of this current moment in time Lambda supports runtime versions for Node.js, Python, Ruby, Go, Java, C# (.NET Core), and PowerShell (.NET Core).
In this blog post i’ll show you how to create a function that removes objects from CloudFront edge caches around the world after an object has been uploaded to an S3 bucket and create an SNS topic that sends an email notification once the CloudFront has been invalidated.
Requirements
• Existing S3 Bucket
•The Lambda function that you will create needs to reside in the same region as the existing S3 bucket that will be used as an event source.
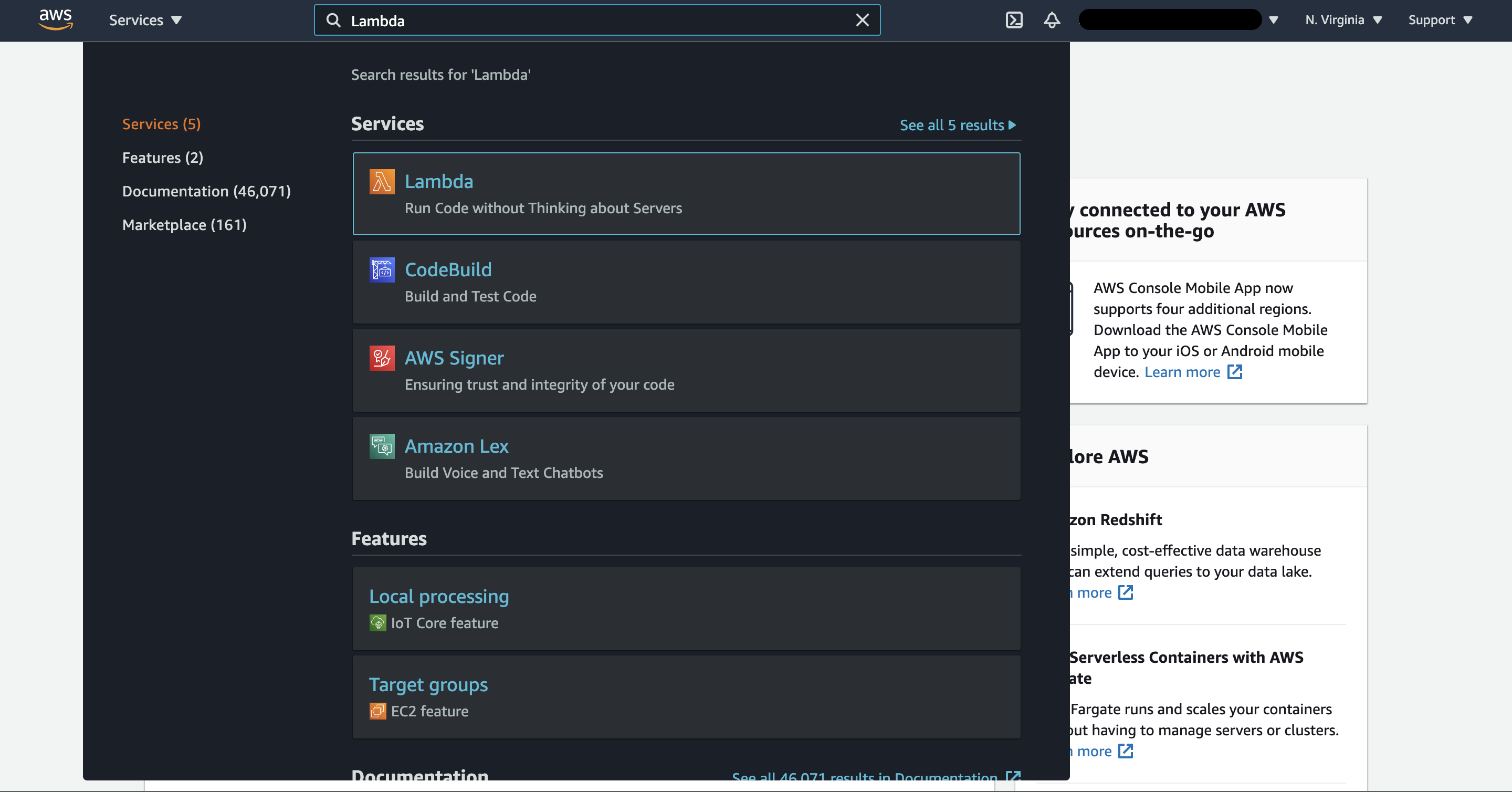
Once you have logged into the AWS management console, search for Lambda in the main search bar and select the service from the list of services displayed.
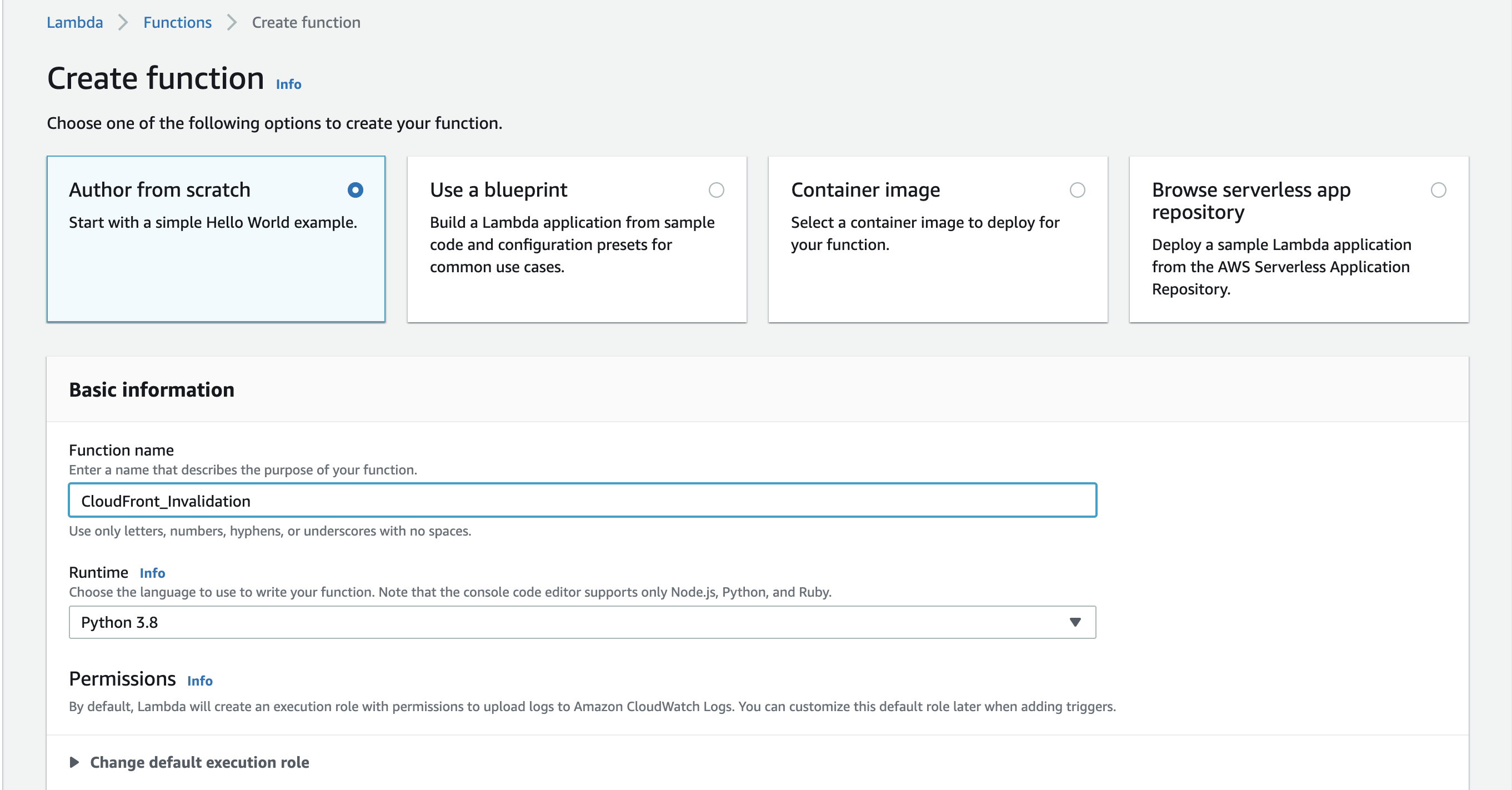
Select the Author from scratch tile and provide a name for the function as well as choosing the Python 3.8 Runtime. Leave the existing default settings as is and proceed by clicking the Create function button.
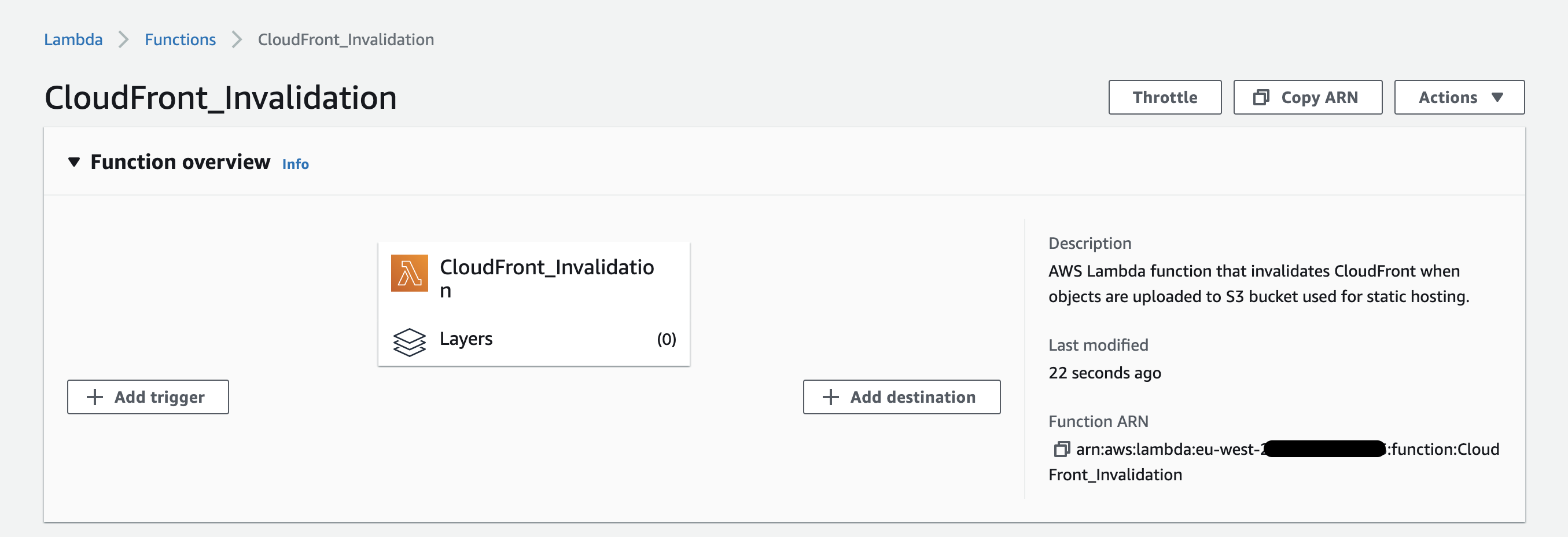
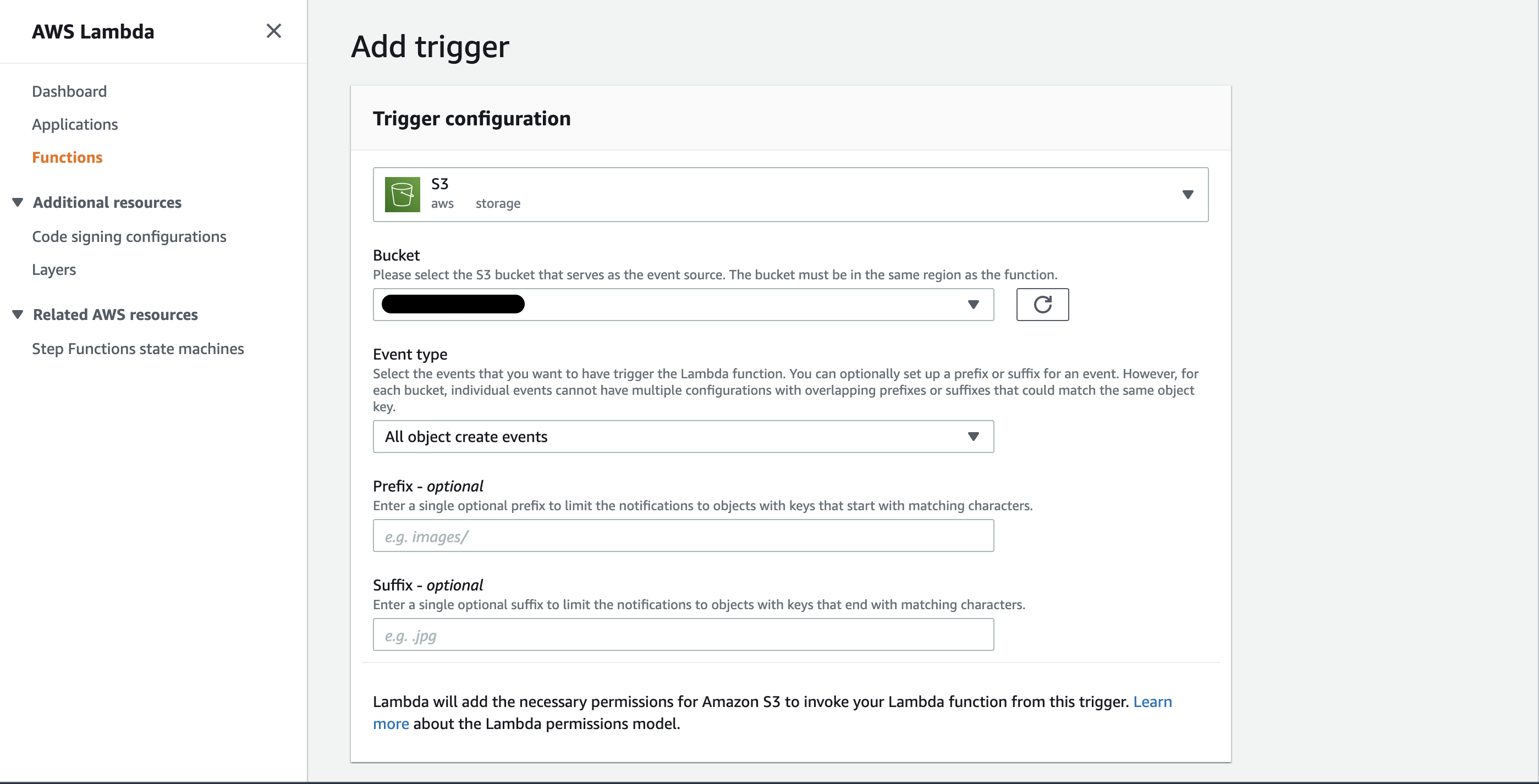
From the main Function overview, select Add trigger.
From the next page search for S3 in the Trigger configuration dropdown and select the bucket that will be used as the event source. For the sake of simplicity select All object create events from the Event type dropdown. Acknowledge the Recursive invocation banner at the bottom of the page and select Add.
Scroll down the page till you reach the Code source widget.
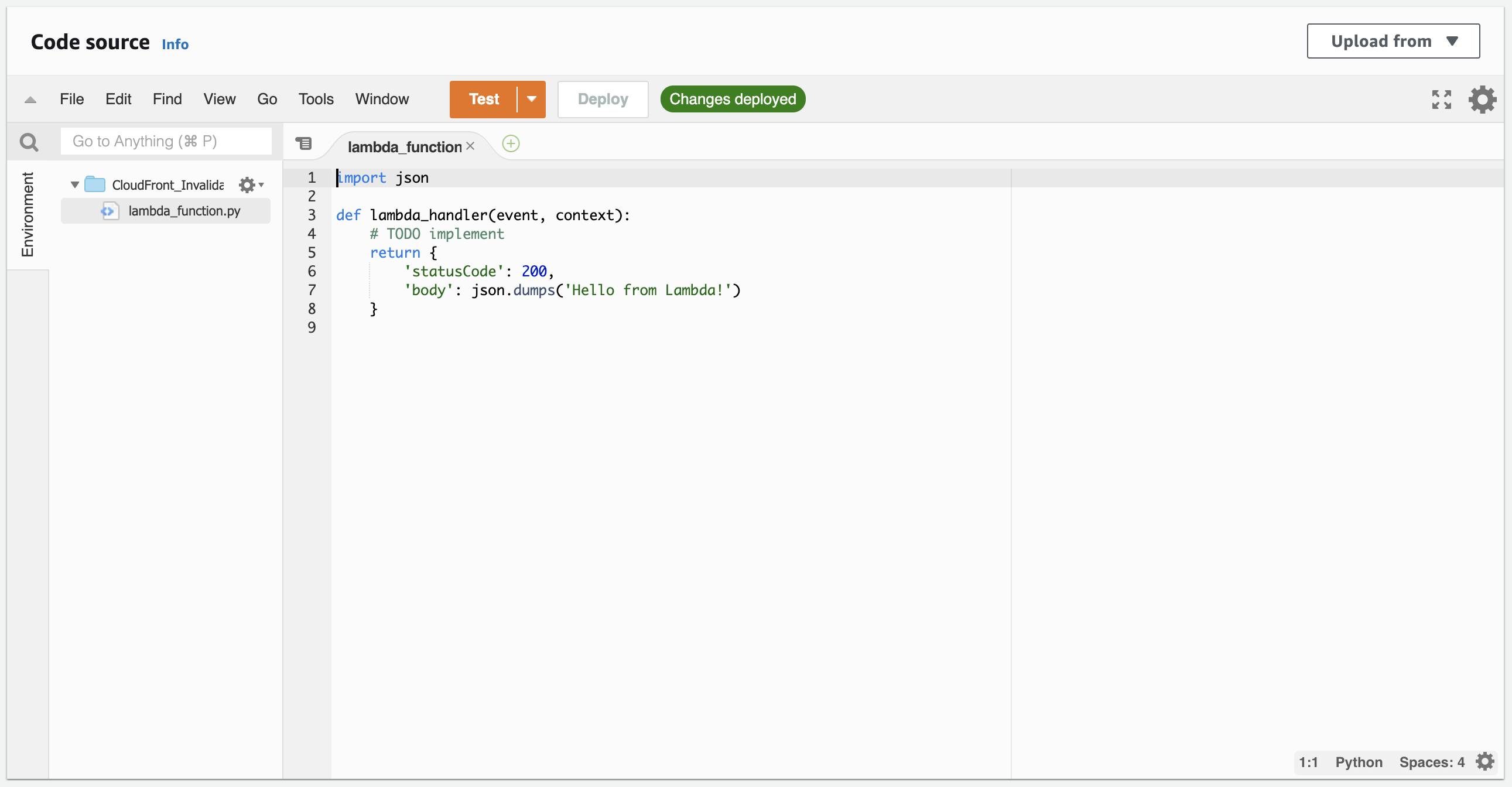
I’ve added the code that you can replace in the on screen code editor. You’ll only need to enter the Distribution ID value of your CloudFront distribution. Once you’ve added the code select Deploy.
Invoke the Lambda Function
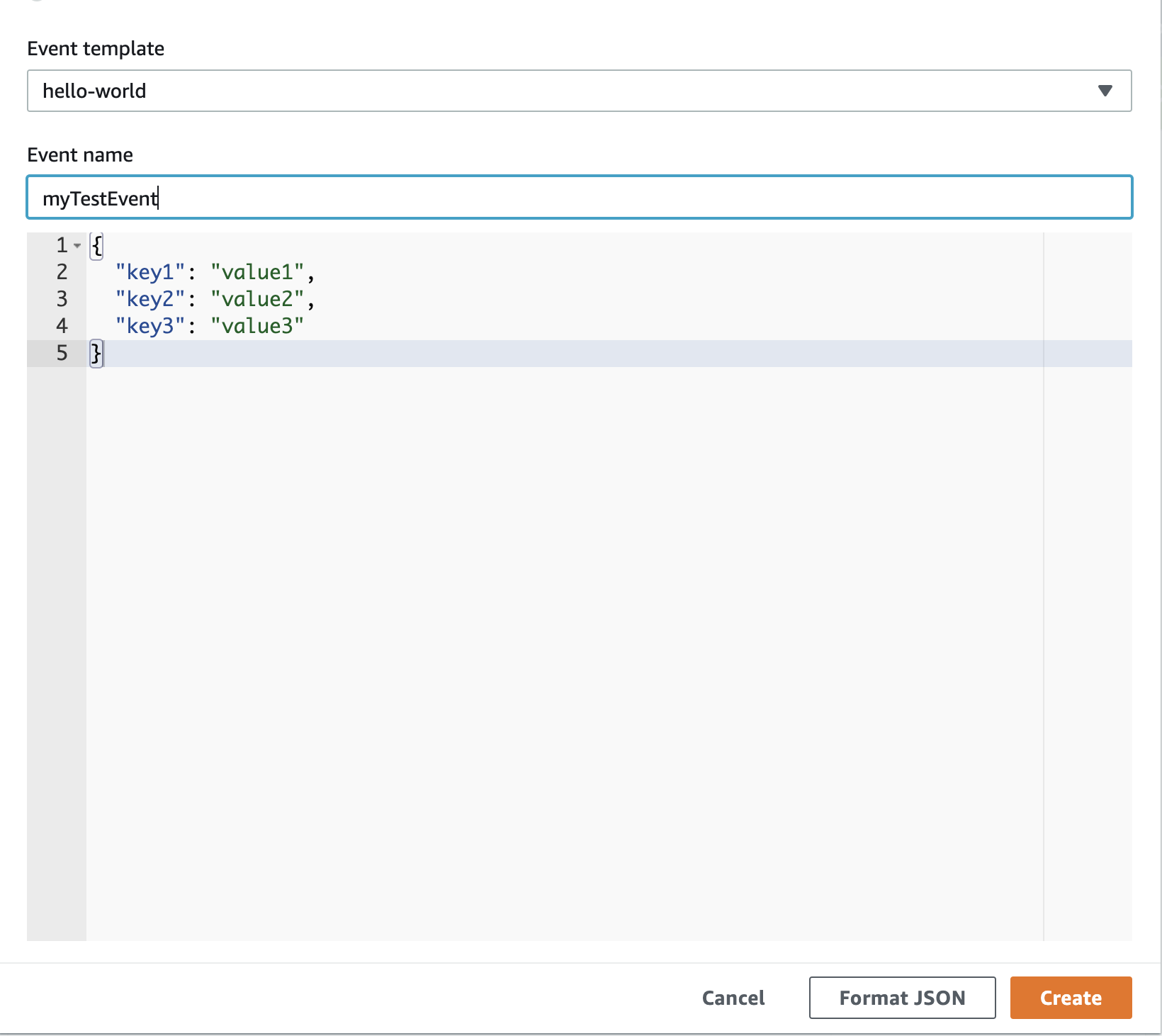
From within the Code source widget select the Test tab and select Configure test event, select hello-world from the Event template dropdown, lastly you will need to provide a name for the Event and select the Create button.
Once you have created the test event, select the Test button, the test should execute the Lambda function on your behalf. You’ll notice that a Failed status is returned.
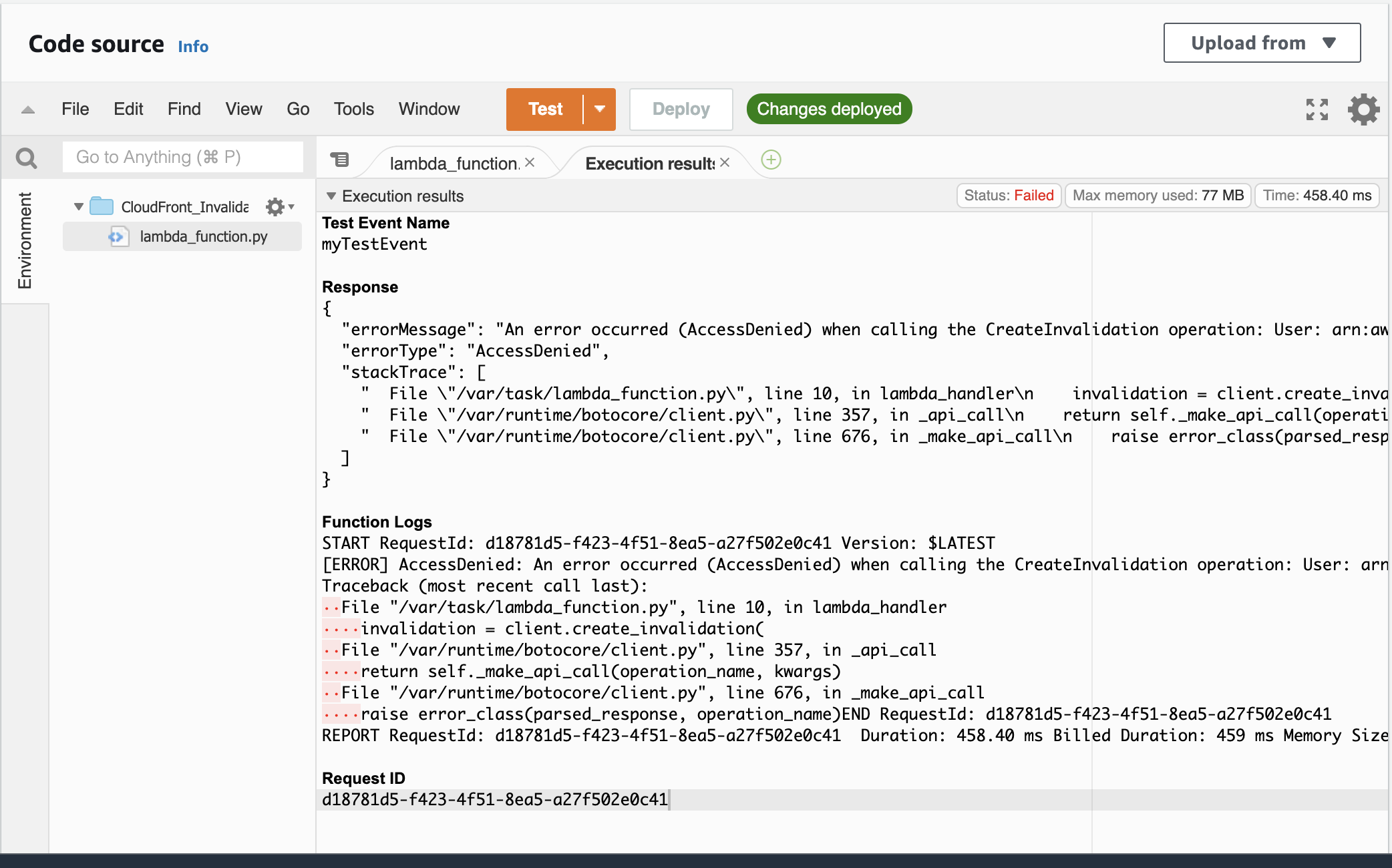
In order for Lambda to be able to invalidate CloudFront, a role needs to be created with permissions that will grant it access to the AWS service on your behalf.
The next step is to create a role by navigating towards IAM and selecting roles from the left-hand pane.
Select Create role, from the proceeding screen select AWS service from the type of trusted entity and select Lambda from the list of services.
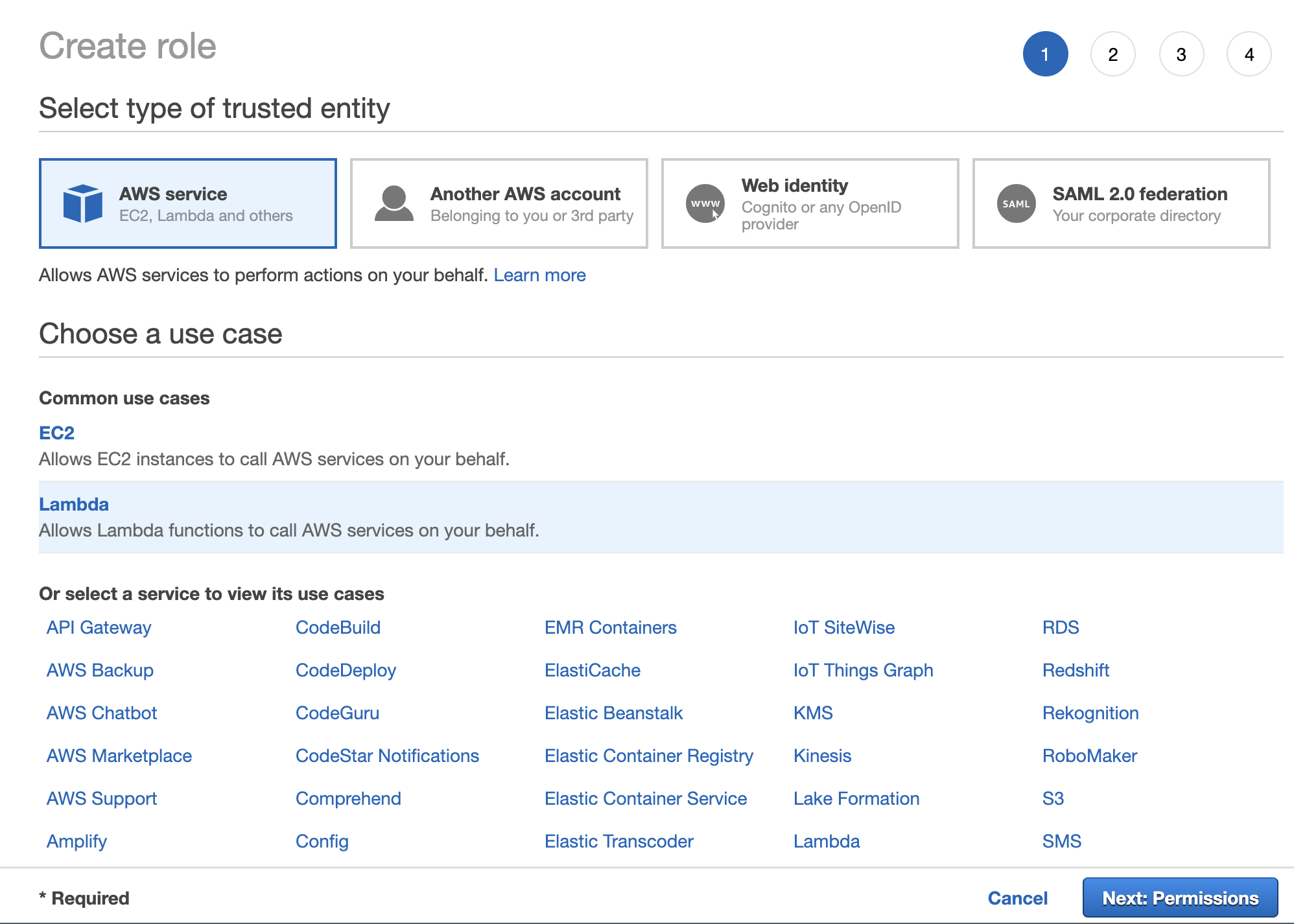
From the next screen, select the Create policy button. We will use the visual editor to create two policies, the first of which will allow Lambda the ability to invalidate CloudFront and the second policy will allow our Lambda function to send logs to CloudWatch.
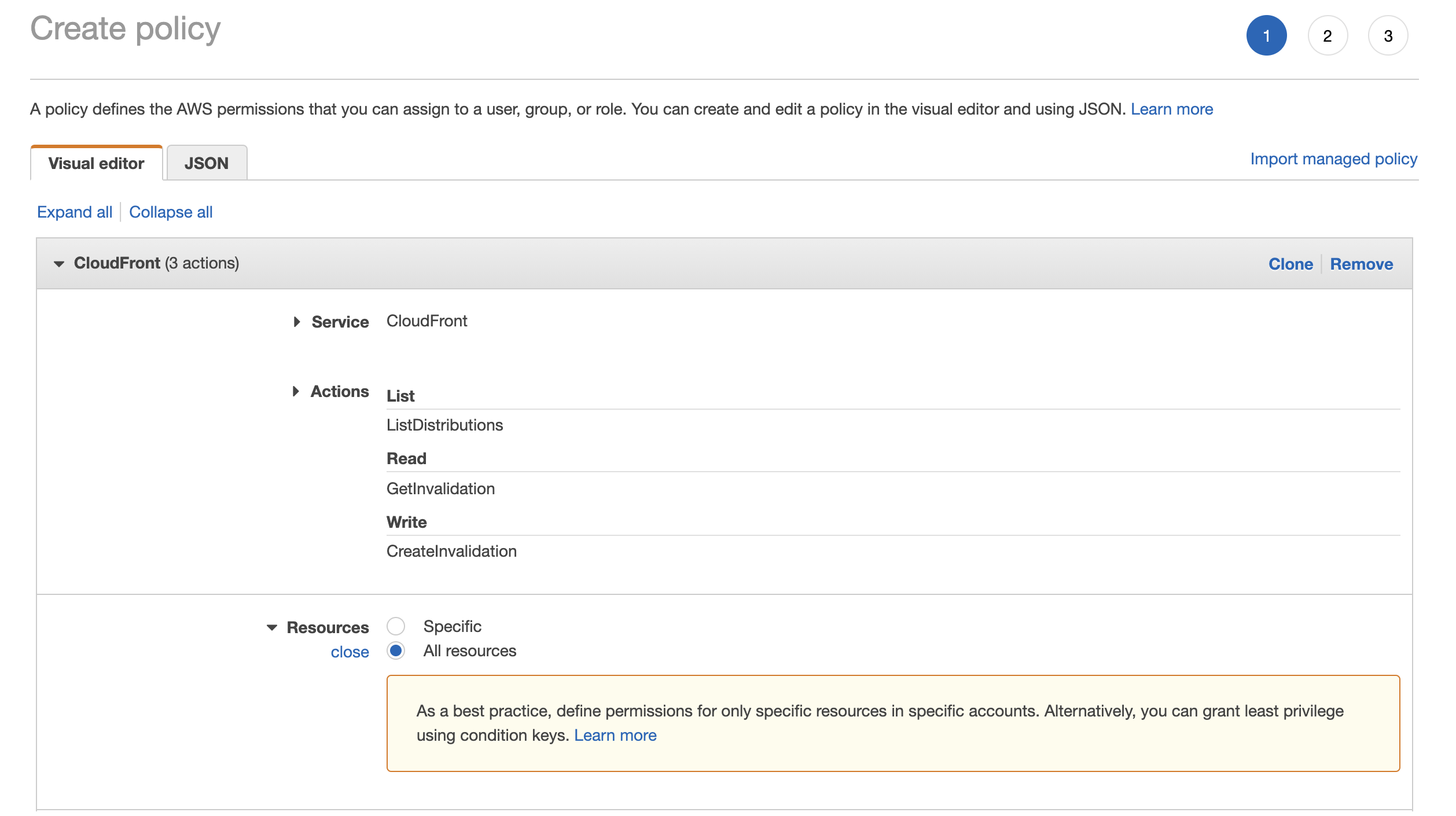
A new tab will open in your browser. Search for CloudFront in the search box that appears next to Service. Under Actions, specify the actions (List, Read, Write) allowed that are shown in the below screenshot and specify All resources, in a real world scenario you would define permissions for the specific resource.
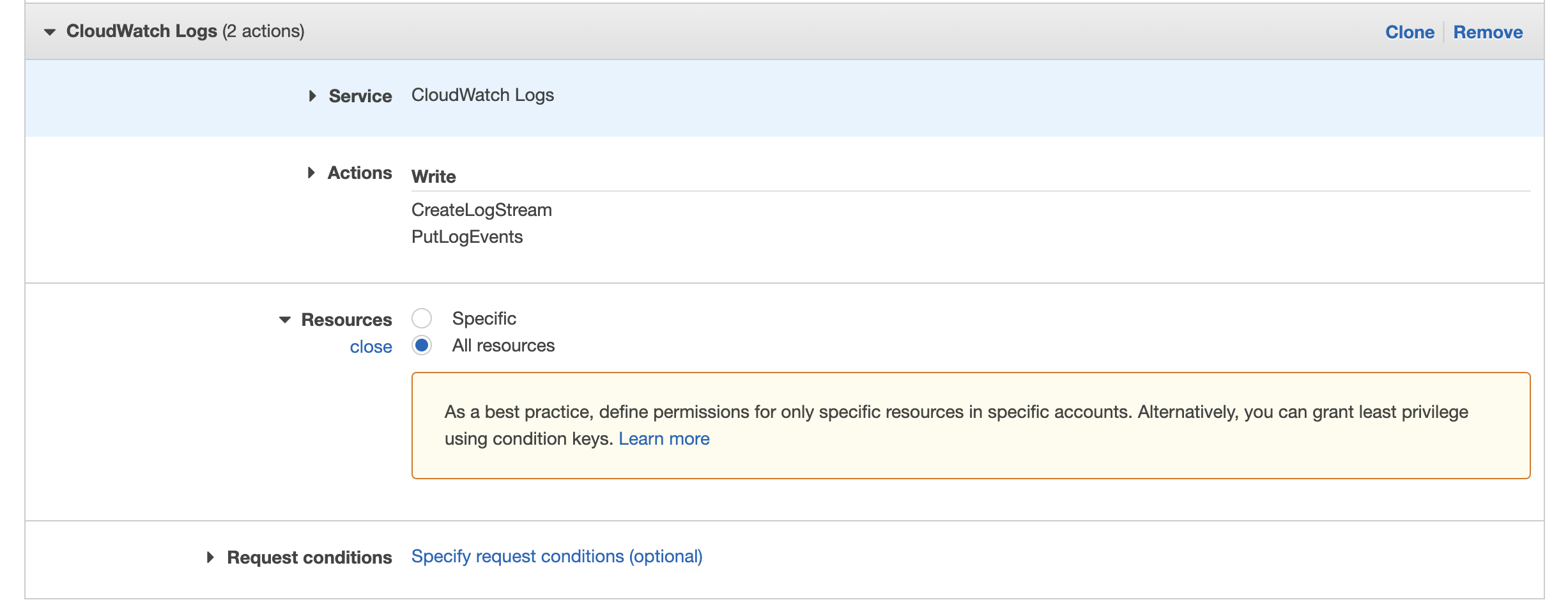
The next policy to create is for CloudWatch Logs, select the + Add additional permissions button and ensure the policy has the same configuration as the screenshot below:
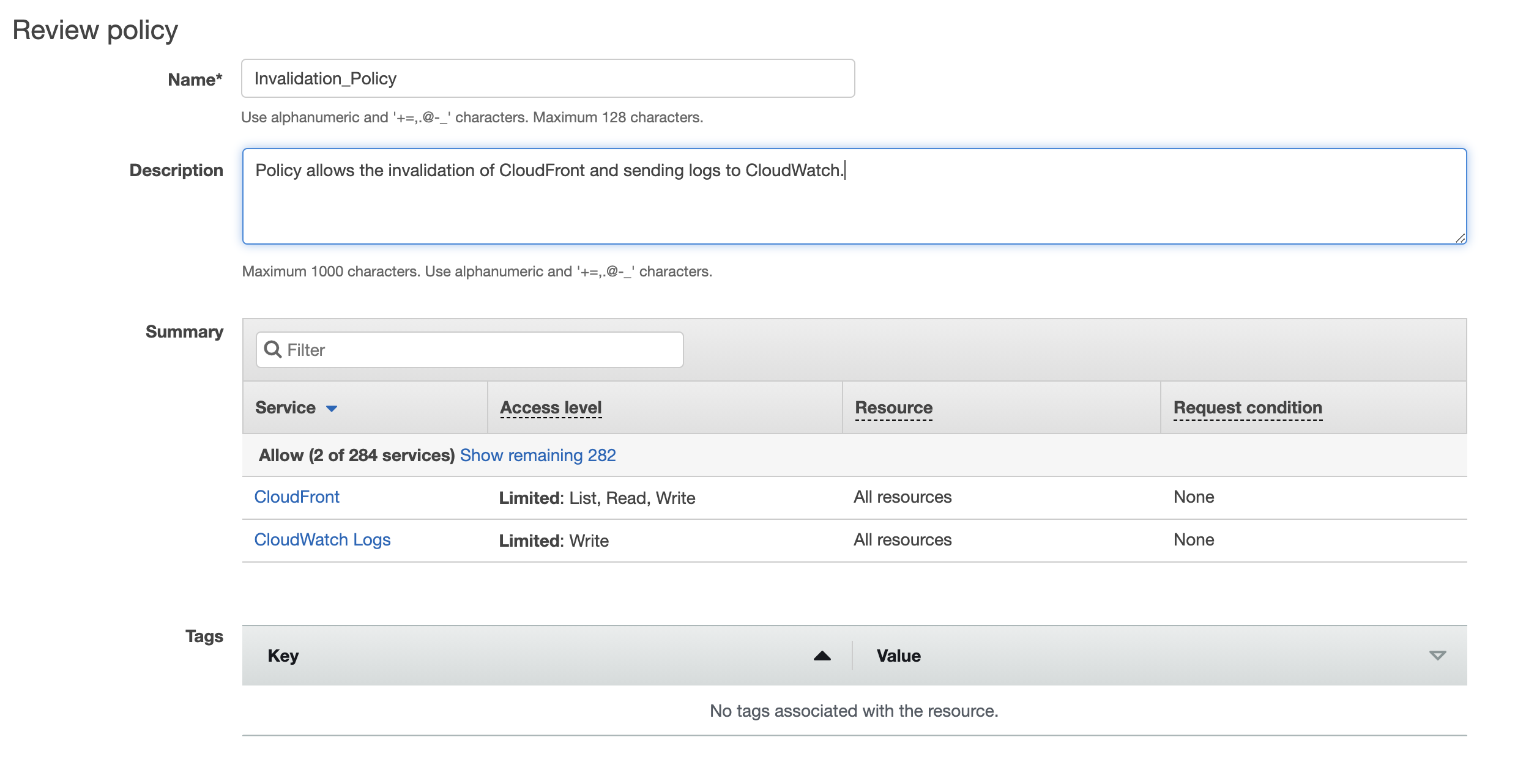
On the Review policy screen, provide a name for the policy and a description.
Once you have created the policy, navigate back to the previous tab, search for the policy and select it.
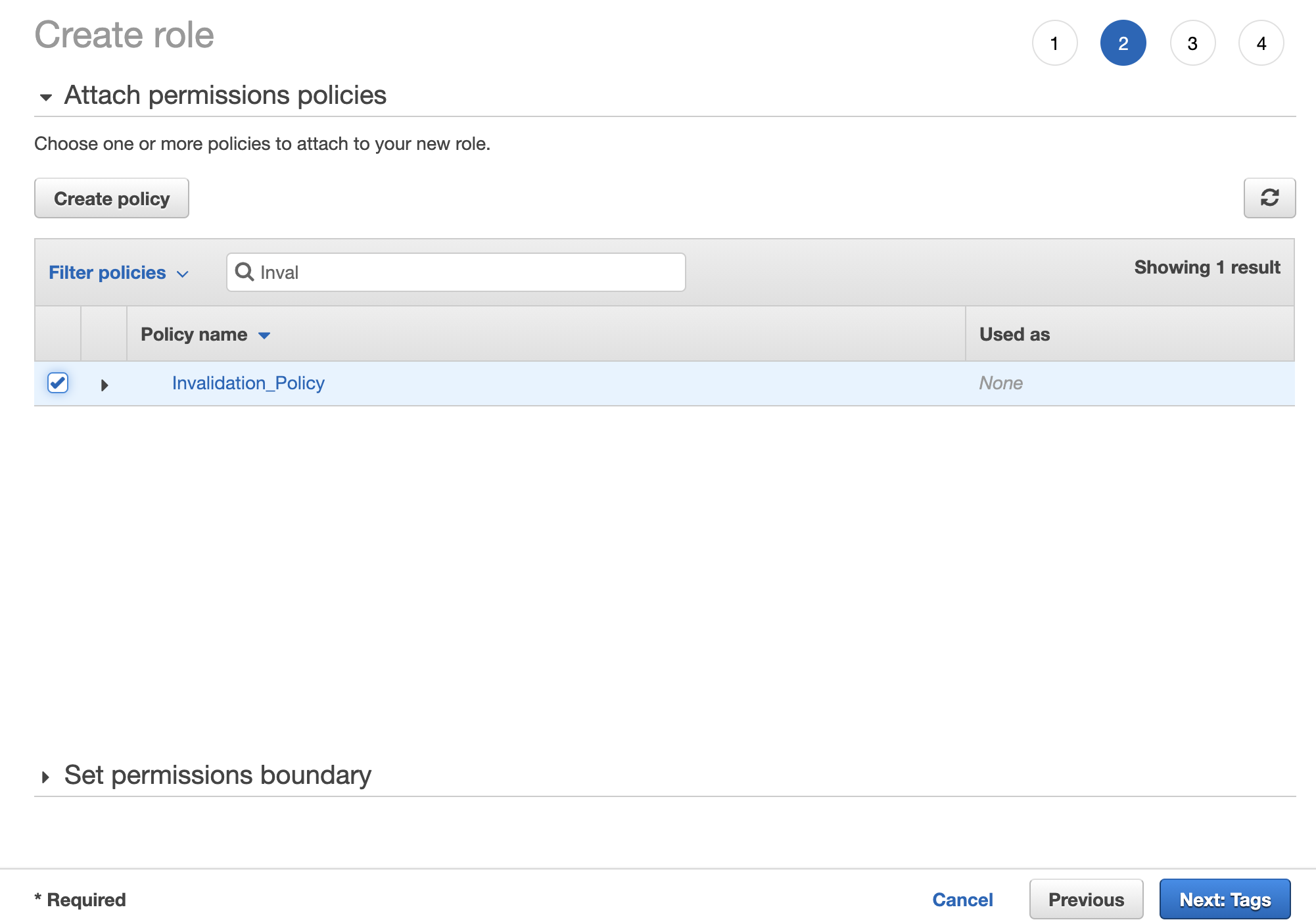
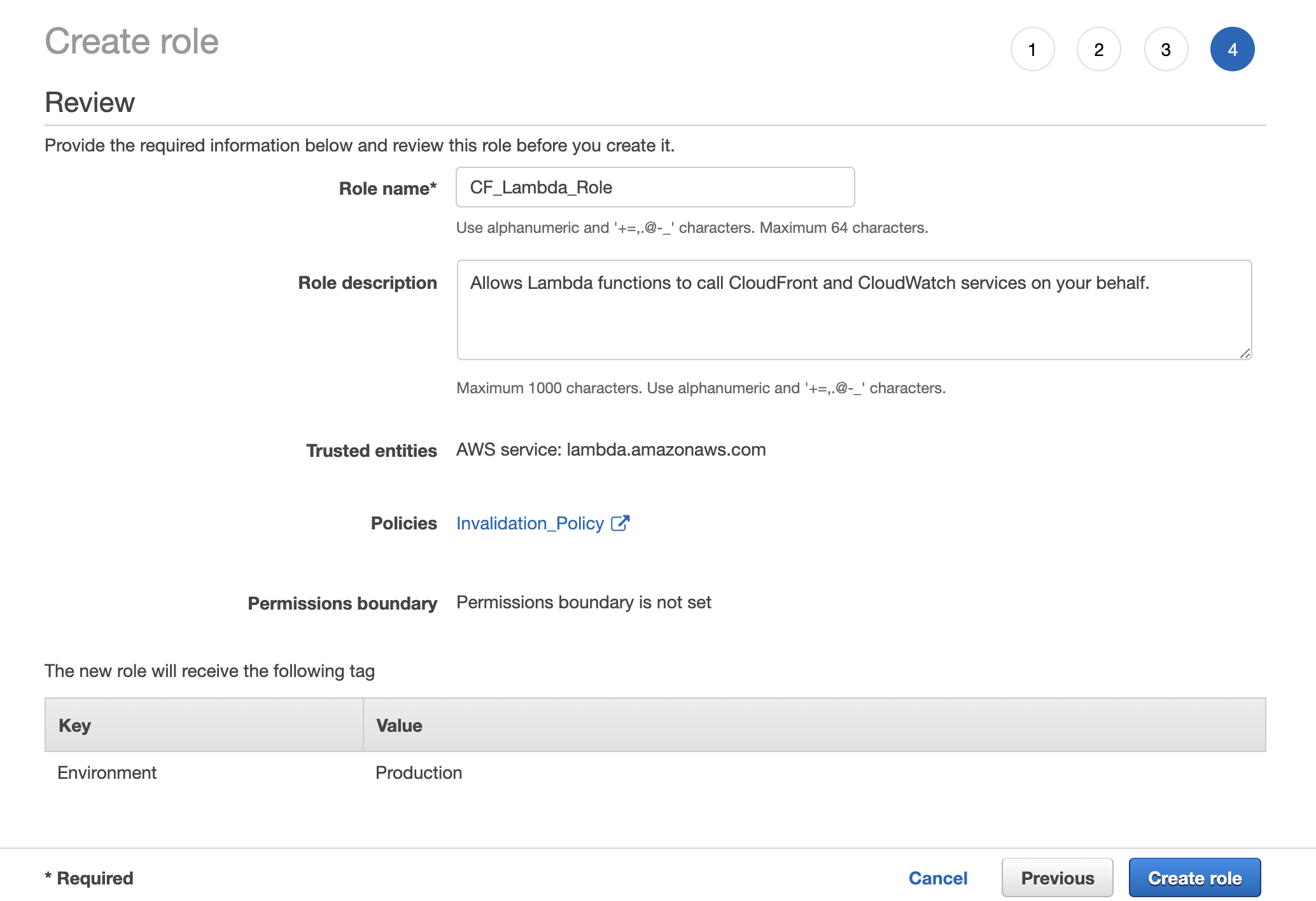
At the last screen you’ll need to provide a name as well as a description for the role you are about to create.
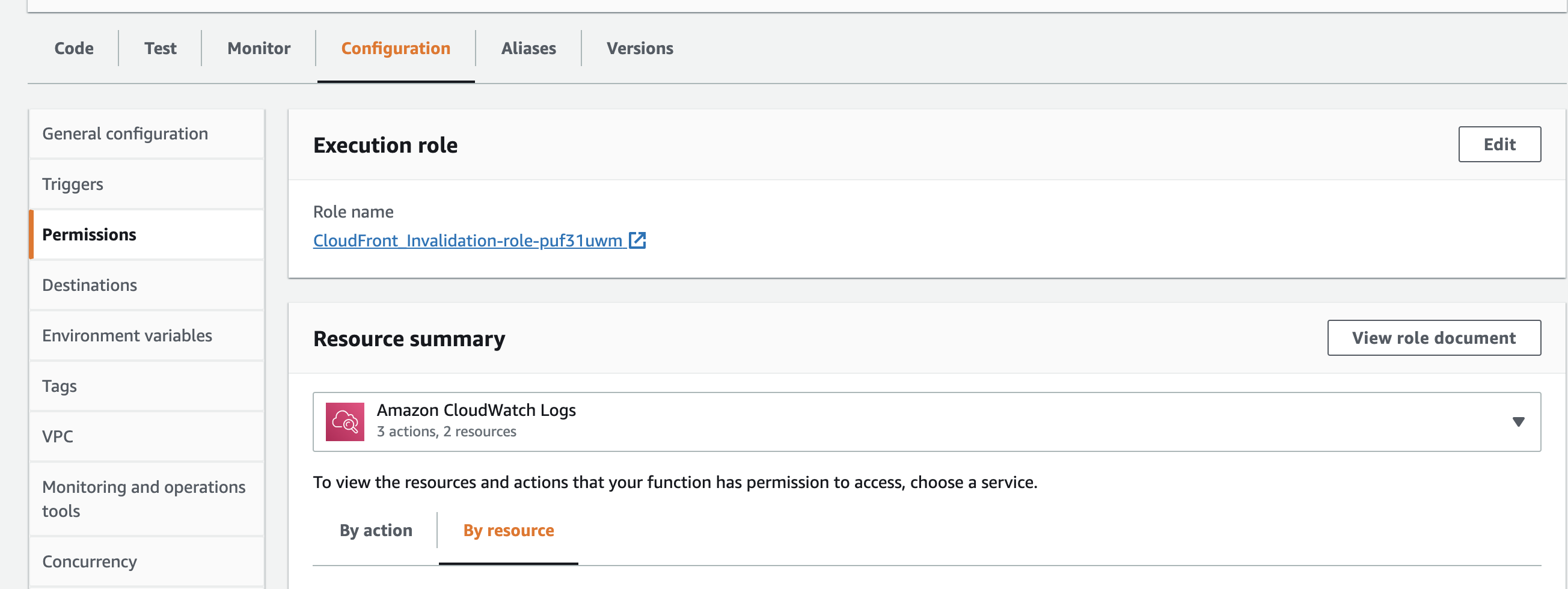
Navigate towards the Lambda function you created earlier and under the Configuration tab, select Permissions, select Edit under Execution role.
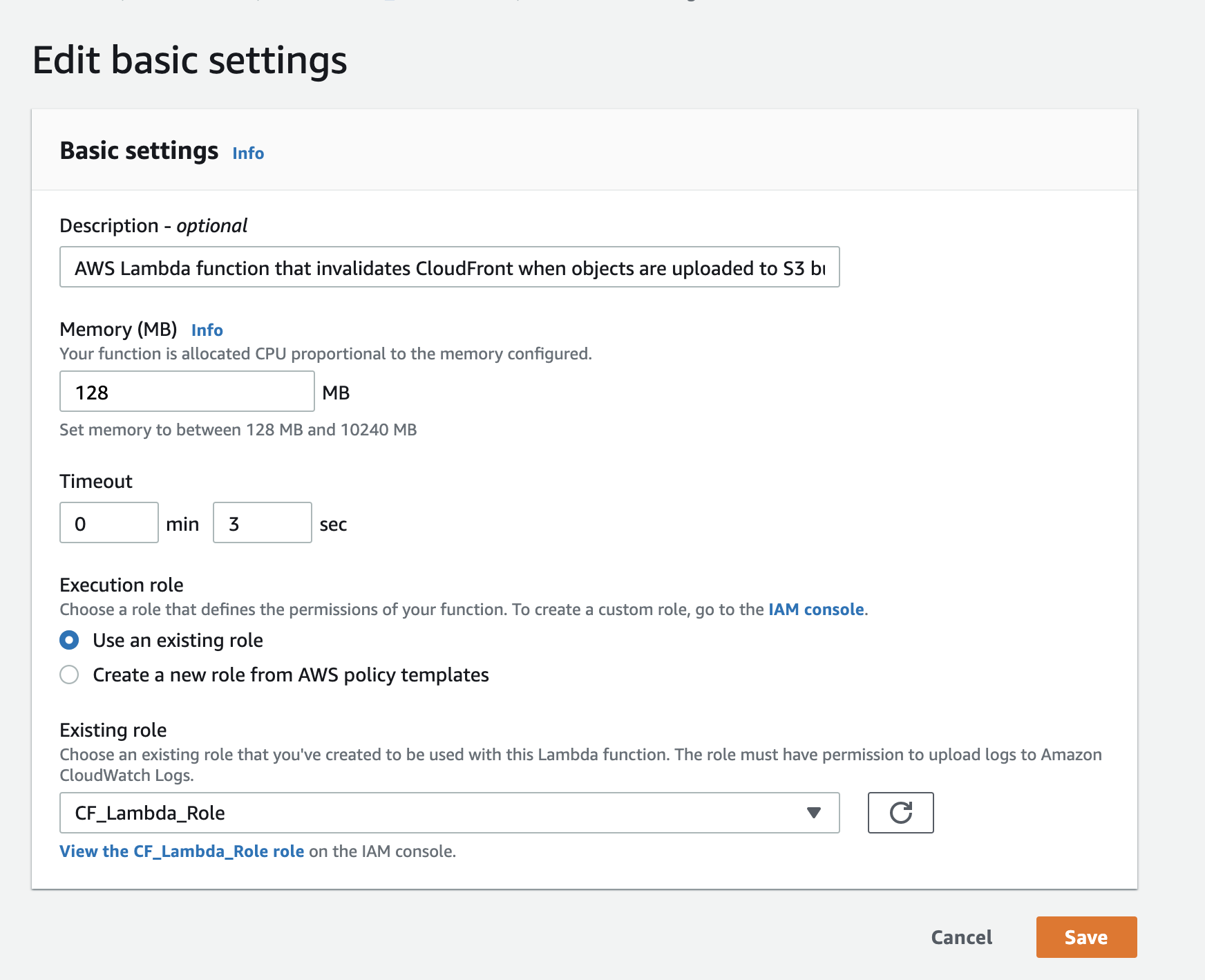
At this step we will use the existing role we created previously and save the settings.
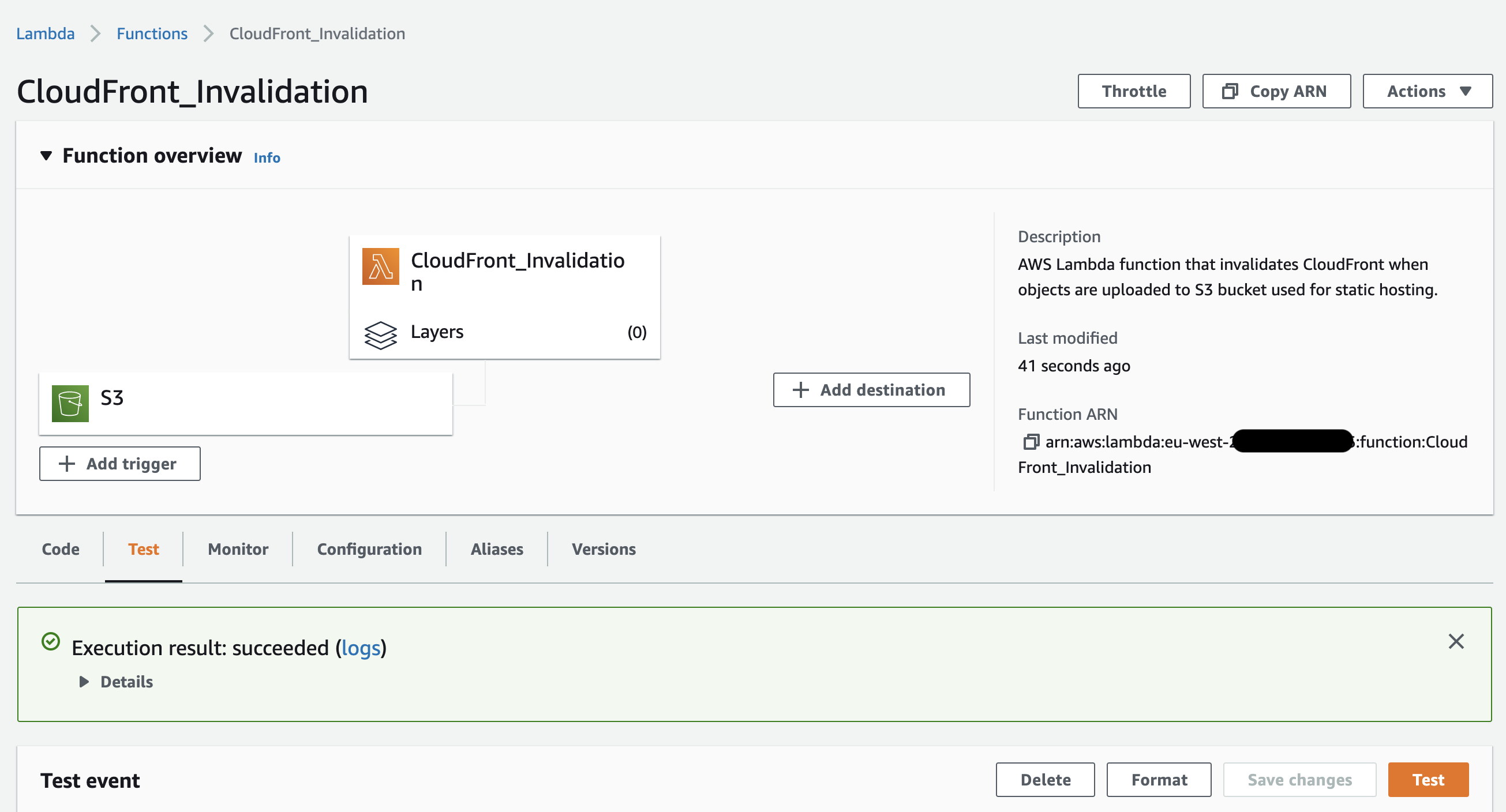
It’s time to invoke our Lambda function again, this time around our test should succeed as evident in the below screenshot.
SNS (Simple Notification Service)
The last component of this solution is the implementation of SNS. This will notify us via email when our function has been successfully invoked.
Amazon SNS is a managed messaging service that lets you decouple publishers from subscribers. This is useful for application-to-application messaging for microservices, distributed systems, and serverless applications.
Navigate towards SNS, select Topics and create a topic.
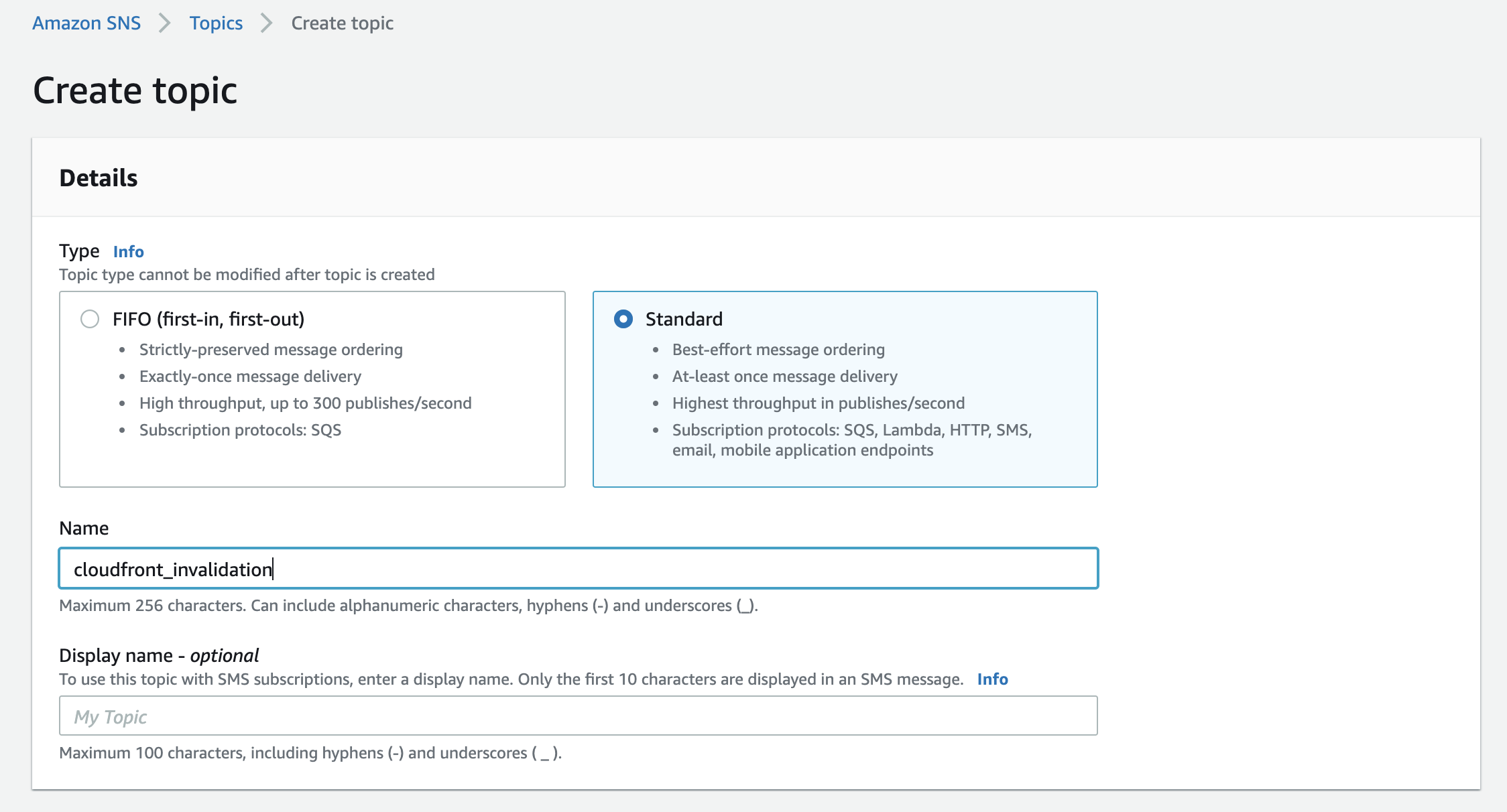
At the next screen, select Standard for the Topic type and provide a name.
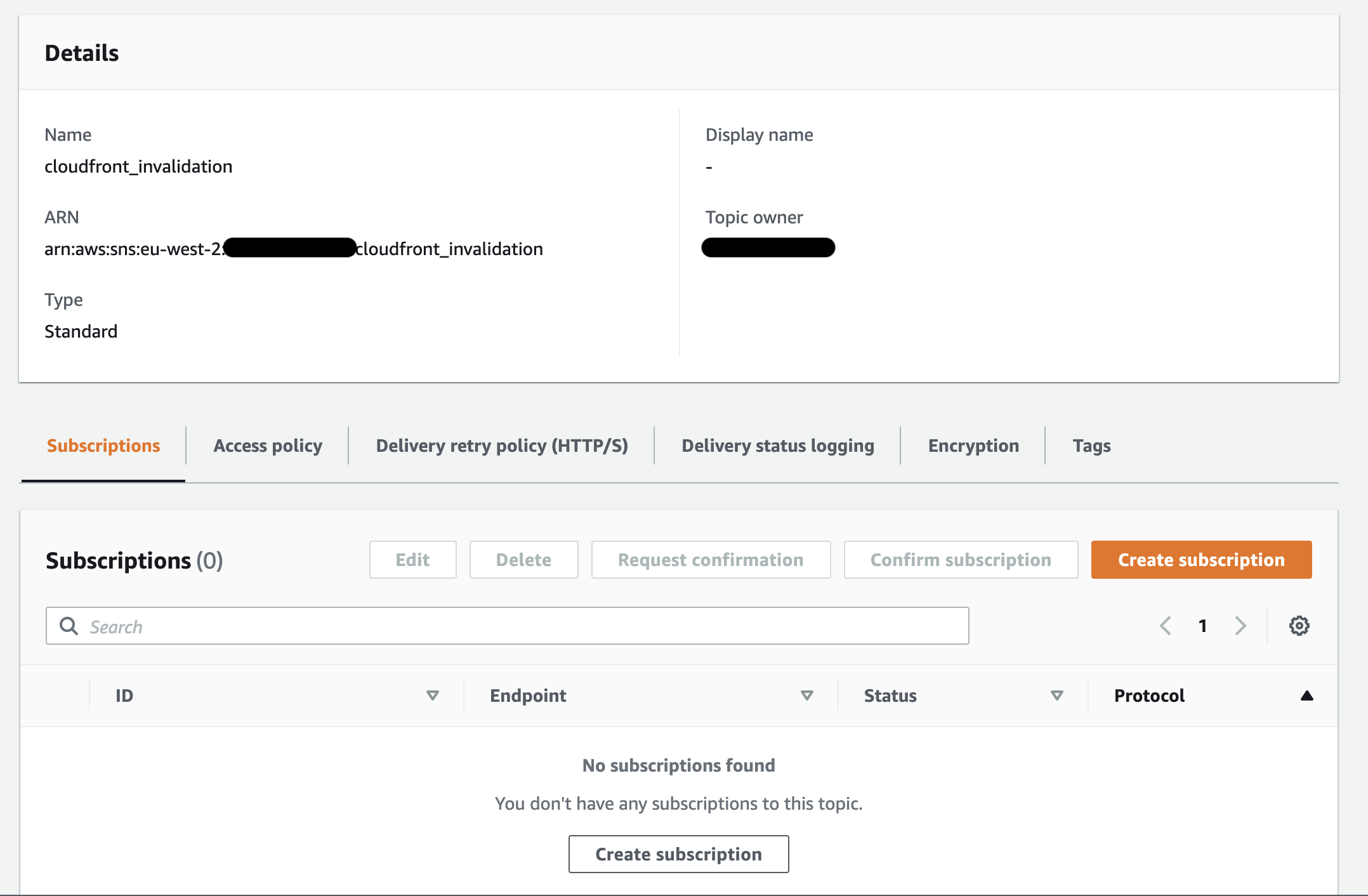
You’ll need to create a subscription and choose the type of protocol you would like to subscribe to, in this case select email, input your email address and confirm the subscription.
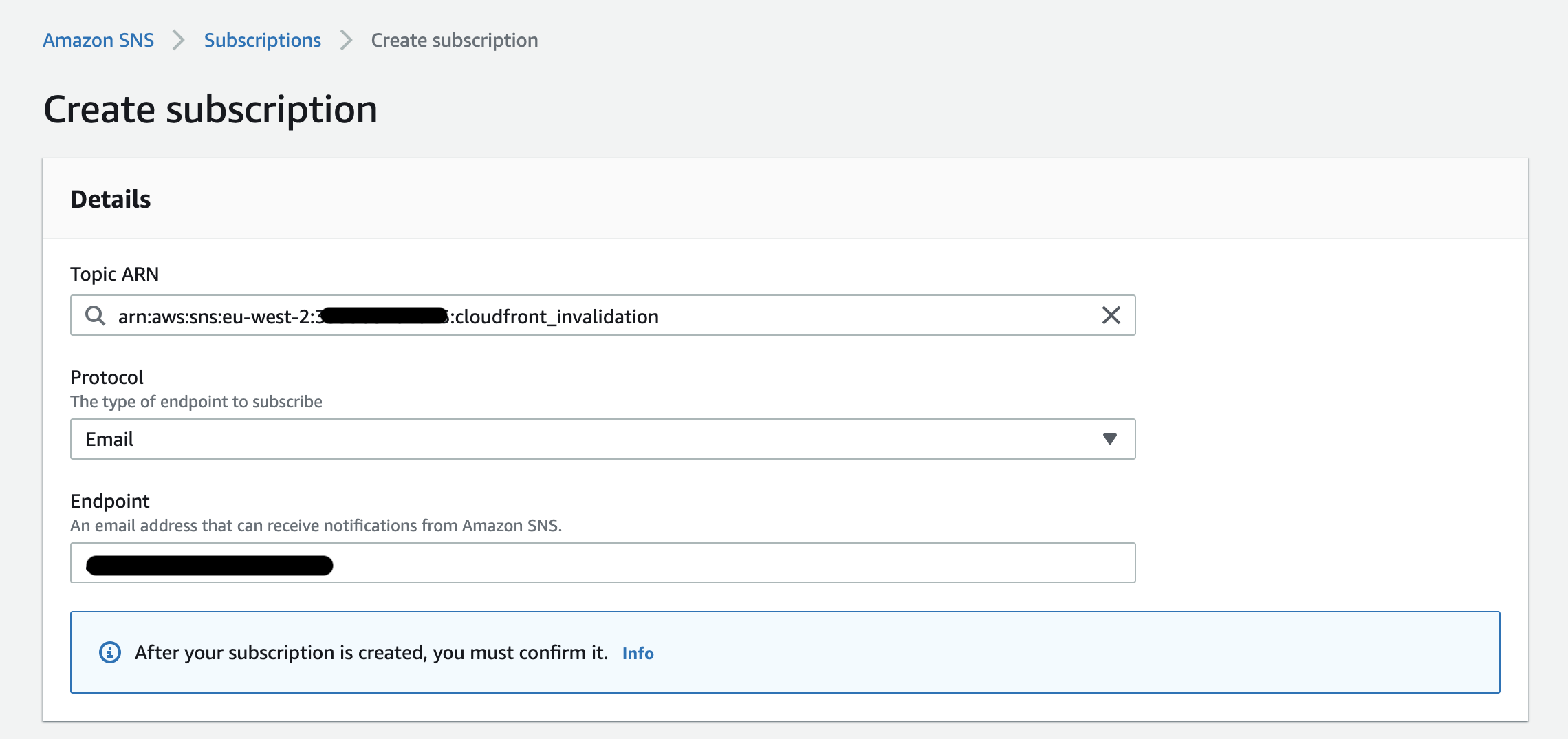
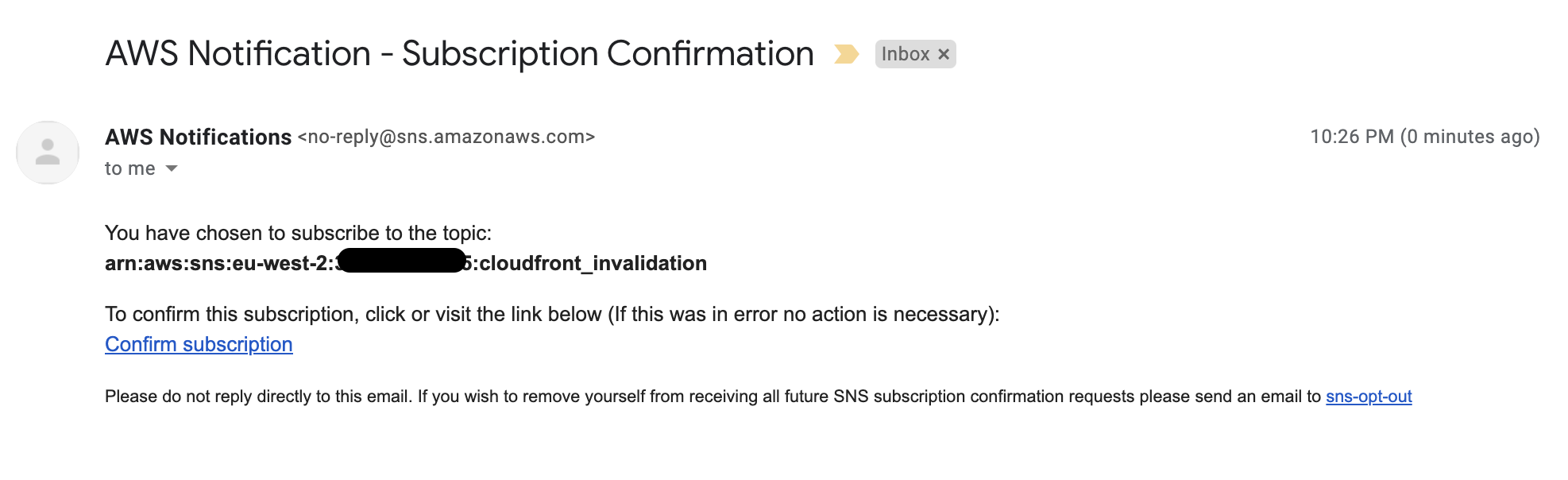
Navigate back to the Lambda function… we’re almost done.
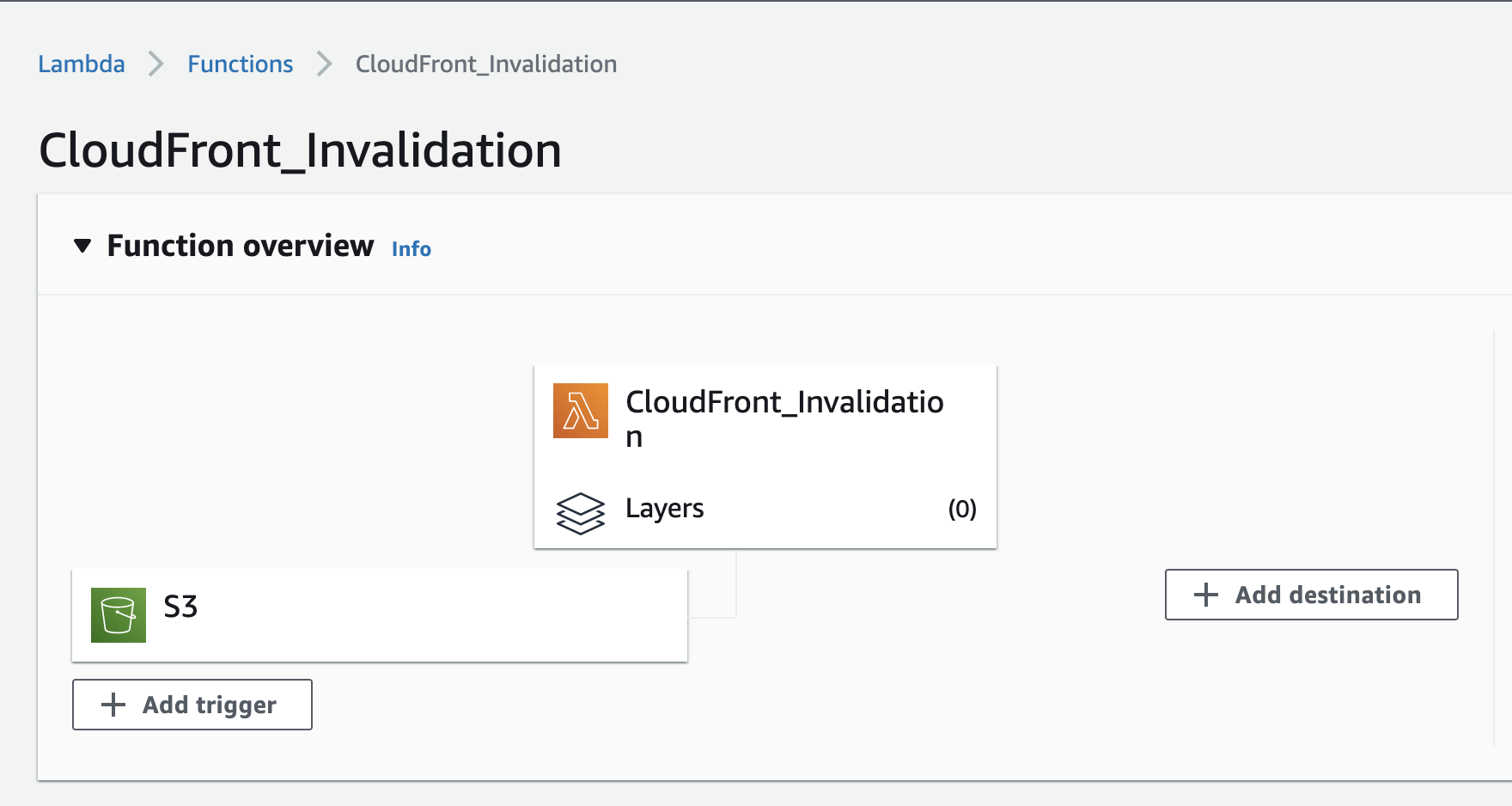
The last step is to select the SNS topic created in the previous step, select + Add destination under the Function overview widget and ensure that the condition is set to On success and save the destination configuration.
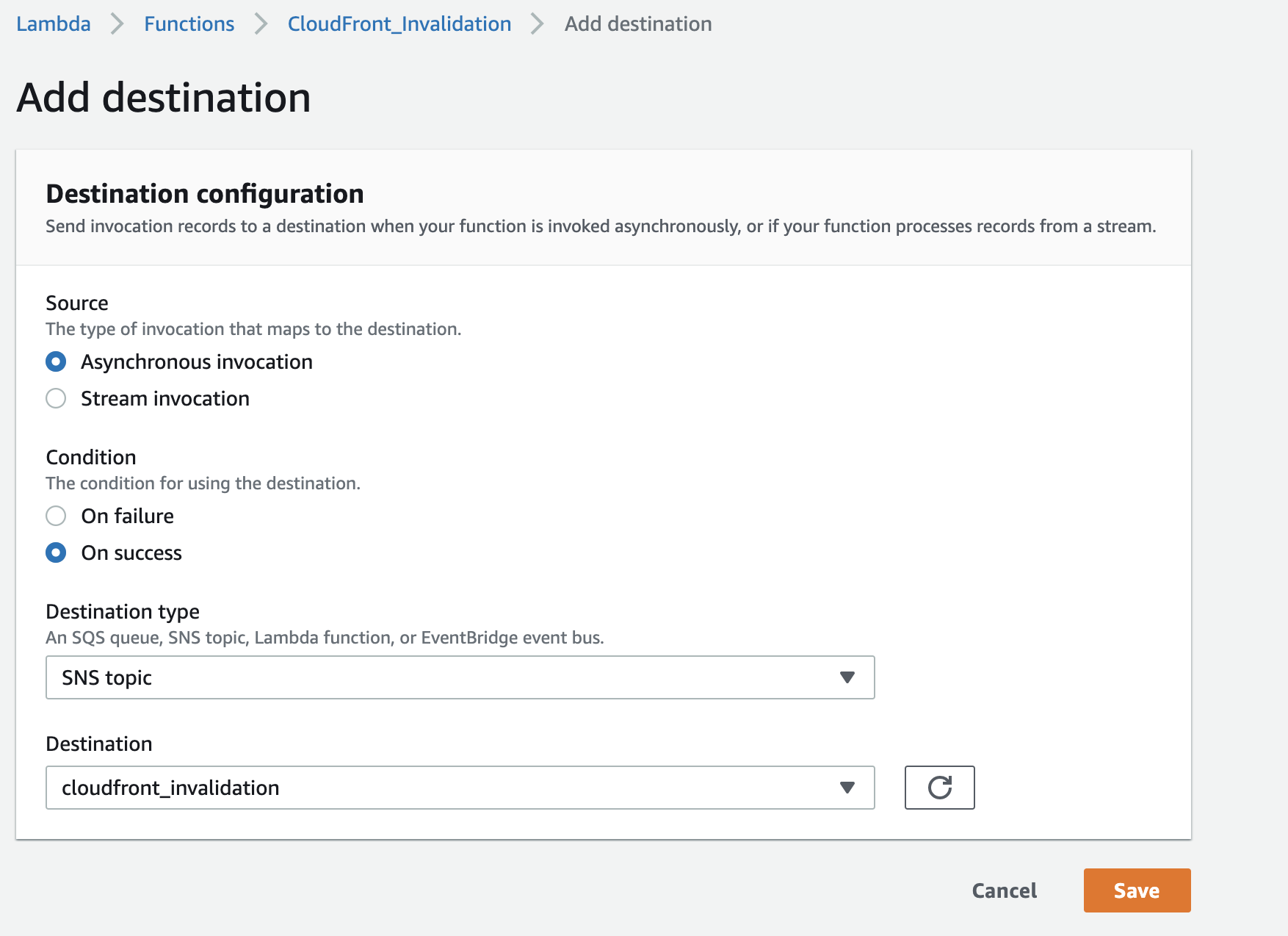
Our solution is now complete. It took a while.
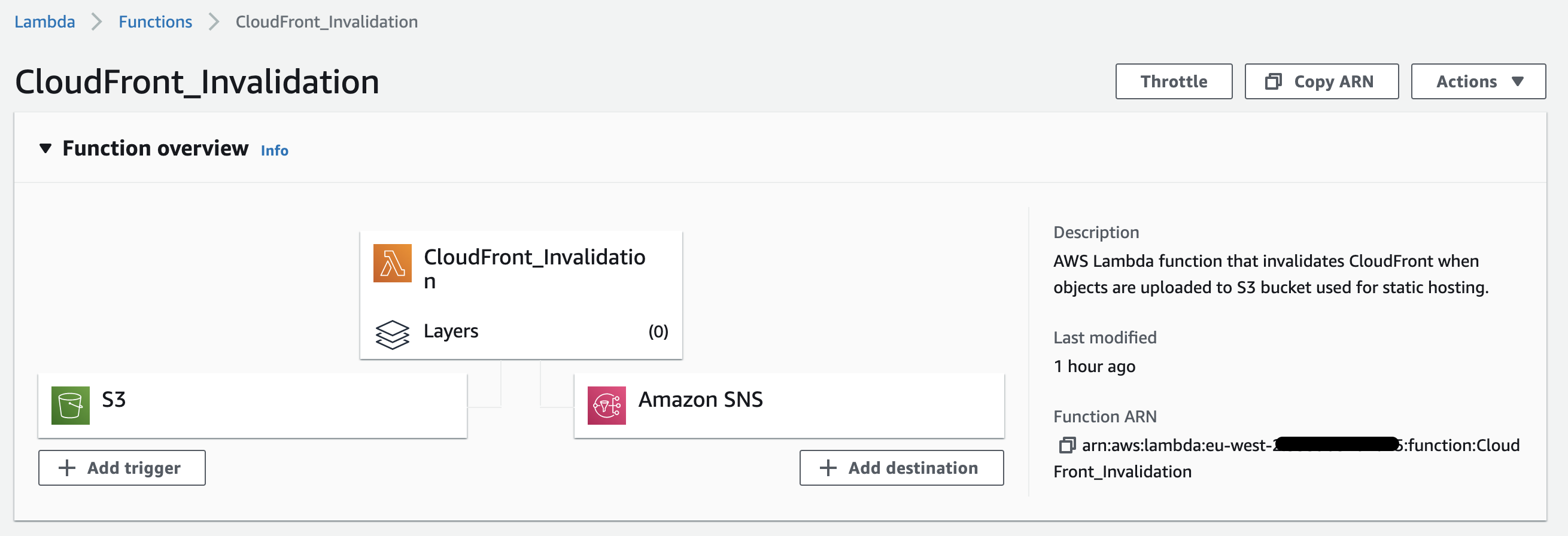
You can now upload an object to the S3 bucket you had selected as the source trigger at the beginning of the tutorial to invoke the Lambda function.
You’ll receive a JSON payload in your email inbox once the Lambda function has been successfully invoked.
That concludes this post. I hope you’ve learnt something new, if you’re keen on a challenge you could clean up the format of the message sent from SNS.
The Power Of Lambda - A serverless approach to invalidating AWS CloudFront